Identifying Additional Permissions for Users¶
As a Altair SLC Hub user, you will most frequently access functionality from an external client rather than using the Hub Portal; typically this would be connecting to a Hub instance from Workbench. Connecting in this manner will not provide you with feedback if you attempt to use functionality for which permission has not been granted.
Altair SLC Hub permissions control various aspects of the access to and use of Hub, and you need to be a member of multiple Hub user groups to provide the access you require. When you attempt to access functionality where you do not have permission, that action is recorded in the Access Control log. If you are attempting to access functionality for which you should have permission, the Hub administrator can use the Access Control log to track this activity and modify your permissions as required.
The Access Control log is available in the Hub Administration section of the Hub Portal. This view provides a list of every interaction for all users with the Hub instance. You can filter the listing by object, action, decision, purpose, user, and duration of the logs.
A Hub installation contains a set of default groups that provide different levels of permissions for the functional areas of Hub.
For example, to use defined libraries in a SAS language program, you should be a member of the HubUsers group to access the Hub instance and DataAccessConsumers to view and use the defined libraries.
The reference of these groups and their permissions can be used to identify the required group or groups for other permissions, see Default groups.
Example: Add Permissions to run SAS language programs
Add the ability to run SAS language programs for a Workbench user (for example, HubTestUser) who can access Hub (create a link session), but cannot run a program (access to the /LinkSessions Object).
Where the user has attempted to run a SAS language program and failed, the Hub administrator will need modify their permissions.
- In the Hub portal, launch Hub Administration and open the Access Control log.
By default, the log displays the last 25 interactions with Hub which might not contain details of the failed attempt. - Using the log filters, restrict the view to the required user (
HubTestUser) and the Decision made to Deny.
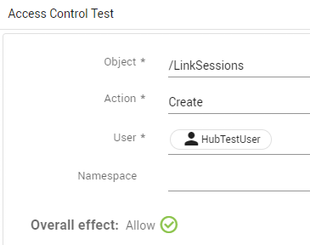
This will show all actions made by the user for which they do not have permission. - Select the most recent log entry that denies access to the
/LinkSessionsobject. Click the three dots and click Test. - In the Access Control Test window, click Test Access to confirm that the permission is not available:
- Click Groups in the menu and search for the
LinkSessionUsersgroup.
This group provides the associated users with the Create action for the/LinkSessionsobject. - In Group members, click Add.
Then in the Add members dialog, enter the user name as displayed in the Access Control log (HubTestUser), in the search field and click Add next to the user's name in the list. - Close the dialog and click Access Control Log in the menu.
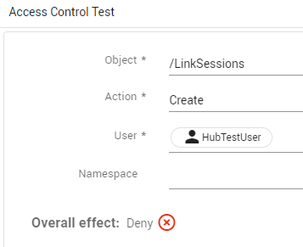
In the log, filter to show the same deny decision located in step 2. Select the entry for the/linksessionsobject and test the connection. The Access Control Test shows the user now has the required permission: